A site for solving at least some of your technical problems...
Bad DKIM signature data
Yesterday I had a customer sending me emails from a different account from last time. That different account is a Yahoo! account so in general there is no problems with that.
Yet, this one time it did not make it. One of my email filters failed. Namely, the DKIM filter. It uses the dkim library to check mail messages and make sure that they indeed originate from where they say they are from.
It is an interesting concept. In the following figure I show the standard scenario of a hacker sending me spam and a valid domain sending me an email:
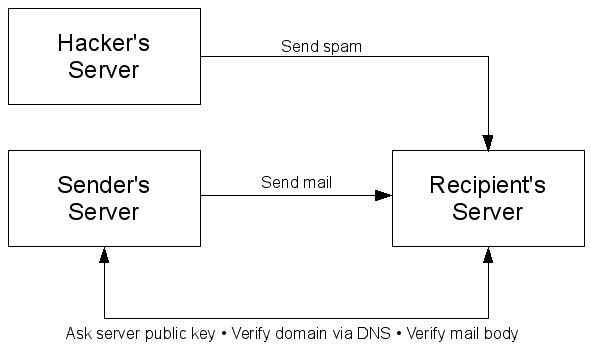
As you can see, if I communicate with the sender's server (via the DNS server) I can ask the domain whether it signs all of its emails. If so and the spam email is not properly signed I can safely discard the spammer's email.
This works in most cases. but with that one customer, it failed...
There are two ways to avoid problems. You can add the whole domain to the peerlist of the DKIM driver. The problem here is that you will accept any email from that domain without verification. Whether or not the emails are from a hacker. Yet, if that domain did not properly implement the DKIM specification, you may not have much of a choice.
The other way is to add the email(s) in a whitelist checked before the DKIM filter. At that point it will bypass the DKIM filter. It won't prevent a hacker from using that very email, but they need to know what's in your whitelist... not as easy.
More info: http://en.wikipedia.org/wiki/DomainKeys_Identified_Mail
Recent Posts on The Linux Page:
