A site for solving at least some of your technical problems...
gVim syntax highlighting failing? (especially for markdown highlighting)
Submitted by Alexis Wilke on Tue, 01/01/2019 - 18:34
Now a days, I write a lot of my documentation using markdown.
The fact is that it is rather difficult to find problems when I make a mistake such as put a lone backtick (`).
Often it feels like the syntax highlighter is failing.
One way to at least make sure that the file fails for real is to make sure that the highlighting starts from the very beginning of the file. To do so you want to change the number of lines that the highlighting works on.
The number of lines is defined in two variables and you probably want to change both of them. Note that to do so, you need to use the :syntax ...
JavaScript async & await, promises, and callbacks
Submitted by Alexis Wilke on Fri, 12/21/2018 - 10:20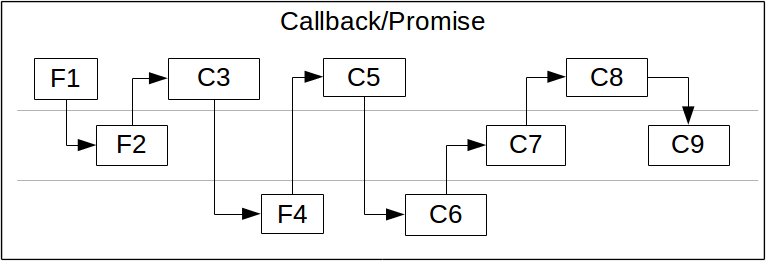
This pictures shows three functions (F1, F2, and F4) and their callbacks (C3, C5, C6. C7, C8, and C9.) The graph shows the order of execution from left to right. As we can see, JavaScript functions and callbacks get executed one after the other. However, the order can seem quite random. This is often referenced as Callback Hell. Promises were going to fix that, but now we have async/await which is even better! Although the execute remains the same (as shown here,) writing the code becomes much more straight forward. For example, changing the graph here with await, it would clearly look like ...
Stars "suddenly" around my mouse pointer under Gnome, Ubuntu
Submitted by Alexis Wilke on Tue, 12/11/2018 - 14:13Today I had a little surprised as stars appeared around my mouse pointer and they remained. I was pretty sure I've seen those before so not too much to worry about, but... how to get rid of them?!
I knew that I just hit something on the keyboard, I just don't really know what the keystroke was. So I want to try that keystroke again and get rid of the stars... Only I have no clue what it is.
Going to the Gnome Preferences:
/usr/bin/ccsm
It appears on the first page for me.
It's called Show mouse. Looking into the settings of the feature, I see that the keyboard ...
Returning a Boolean
Submitted by Alexis Wilke on Sat, 12/08/2018 - 22:21
Introduction
Today I was thinking about returning a Boolean in my JavaScript function.
I do that all the time in C++ because a function that returns a bool is expected to return true or false.
For example, many people in C++ will do:
bool my_func()
{
int t = 3;
...do some computation against `t`...
...now t can be any int number...
return t;
}
The problem with such code is that the returned value is not a properly formatted boolean value. Compilers do it right, but you could imagine that if you return 0x100 and a bool is saved in a byte.
The correct way to do it in ...
Elassandra and the "discover" feature which can't be overwritten!
Submitted by Alexis Wilke on Wed, 12/05/2018 - 01:49
The Problem with Mapping
Today I spent some 3 hours looking into why I could not setup a certain field as text. The newer versions of Elassandra (ElasticSearch, really) makes use of keyword and text instead of string for text-like data. Only, by default the system sees those as list<text> and not just text. I'm not exactly sure why they do that, though.
Anyway, after many questions to Google, I found out that you have to tell the search system that your field is a singleton or it's going to view it as a container of type list. To do that, you just have to add ...
stream_socket_client() fails with no errors...
Submitted by Alexis Wilke on Wed, 11/28/2018 - 11:18
Today I had a weird one.
The PHP function named stream_socket_client(), used to create a socket to communicate with another computer over a network, may return $errno = 0 and $errstr = "".
The PHP reference actually mentions the problem:
On failure the errno and errstr arguments will be populated with the actual system level error that occurred in the system-level connect() call. If the value returned in errno is 0 and the function returned FALSE, it is an indication that the error occurred before the connect() call. This is most likely due to a problem initializing the socket. ...
The HTTP Authentication header is missing / not sent to my CGI script, why?
Submitted by Alexis Wilke on Mon, 11/26/2018 - 11:39
If you are using Apache2, you may notice that the HTTP_AUTHORIZATION is missing from the list of variables sent to you. This is because Apache2 decides to not send clear passwords (even if base64 encoded) across processes.
In the old days (and the capability is still available), Apache would call processes with command line parameters as the data, instead of having environment variables.
Unfortunately, they decided to keep things that way when they switch to FastCGI. So you do not get the Authorization header passed down to your CGI scripts. Whether you use Node.js (through CGI-Node, for ...
How do I know whether a server sends Keep Alive signals over a TCP connection?
Submitted by Alexis Wilke on Wed, 11/14/2018 - 19:17
Today I was curious about whether a certain server was sending me keep-alives.
The fact is that Wireshark is capable of the feat. It has access to the low level data packets and can tell you whether one of those looks like a Keep-Alive sequence (SEG.SEQ) or acknowledgement (ACK).
So if you need to know for a specific server, it's easy enough. You need to connect that specific server and look at the packets using Wireshark.
However, in software, it is not actually possible to determine whether Keep-Alives are being sent. This is because the TCP stack just answers to a signal with a ...
letsencrypt -- The client lacks sufficient authorization
Submitted by Alexis Wilke on Thu, 10/25/2018 - 14:46
Today I had a problem with letsencrypt. I did not want to give me the certificate as it could not verify the domain name I was trying to get a certificate for.
Looking into why I would get the error:
The client lacks sufficient authorization
I only found references to mainly stupid answers. Especially, answers that would tell you to create a directory under the .well-known folder as in:
http://example.org/.well-known/acme-challenge/test
Then make sure you could access "test" by going to that URL.
Sure enough that worked just fine. But it has nothing to do with ...
How do you force the size of a C/C++ struct to a given size?
Submitted by Alexis Wilke on Sun, 10/21/2018 - 17:20Once in a while, I want to create a struct which has a specific size because it has to match a file one to one.
To do that, you can use a simple trick which is to use a union instead of a struct.
union header_t
{
char unused[total_size];
struct
{
int field1;
int field2;
int field3;
...
};
};
Note that the total size of the union may end up being more than total_size. It's up to you to assert that the size does not go over. However, this is an easy way to create a struct which has a hard coded size. However, it will not be ...
Recent Posts on The Linux Page:
